What Is A Network Firewall?
A firewall is a network security device designed to monitor, filter, and control incoming and outgoing network traffic based on predetermined security rules. The primary purpose of a firewall is to establish a barrier between a trusted internal network and untrusted external networks.
Firewalls come in both hardware and software forms, and they work by inspecting data packets and determining whether to allow or block them based on a set of rules. Organizations can configure these rules to permit or deny traffic based on various criteria, such as source and destination IP addresses, port numbers, and protocol type.
Understanding Firewalls and Network Security
Firewalls are the bedrock of network security, shielding the network from unauthorized access. They prevent bad actors — hackers, bots, and other threats — from overloading or infiltrating a private network to steal sensitive data.
Traditionally, firewalls regulate traffic by forming a secure perimeter around a network or computer. This prevents anyone from accessing network resources if they aren’t authorized to do so. Without this protection, virtually anybody could enter and do as they please.
Today's cybersecurity landscape demands a layered approach. While firewalls remain a cornerstone of network defense, advanced threats require additional security measures. The rise of cloud computing and hybrid work environments further highlights the need for comprehensive security solutions.
Fortunately, cutting-edge firewall technologies with AI-powered services are bringing network security up to speed. Combining the strengths of traditional tools with the innovative capabilities of new solutions, modern firewall vendors help organizations defend against even the most complex attack strategies.
What Does A Firewall Do?
Firewalls protect against malicious traffic. They’re strategically positioned at the network edge or in a data center, allowing them to closely monitor anything attempting to cross this boundary.
This visibility also allows a network firewall to granularly inspect and authenticate data packets in real time. This involves checking the data packet against predefined criteria to determine whether it poses a threat. If it fails to meet the criteria, the firewall blocks it from entering or leaving the network.
Firewalls regulate both inbound and outbound traffic, protecting the network from:
- External threats such as viruses, backdoors, phishing emails, and denial-of-service (DoS) attacks. Firewalls filter incoming traffic flows, preventing unauthorized access to sensitive data and thwarting potential malware infections.
- Insider threats like known bad actors or risky applications. A firewall can enforce rules and policies to restrict certain types of outgoing traffic, which helps identify suspicious activity and mitigate data exfiltration.
Firewall vs Antivirus Explained
What’s the difference between firewall and antivirus software? Firewalls focus on controlling network traffic and preventing unauthorized access. By contrast, antivirus programs target and eliminate threats at the device level. More specifically, their key differences include:
Scope
Antivirus software is primarily an endpoint solution, meaning it’s installed on an individual device. Firewalls mainly deploy at the network level, but some organizations install hosted firewalls directly on an endpoint for extra protection.
Functionality
Firewalls monitor traffic, blocking malicious data before it enters the network (or endpoint). Antivirus tools scan the local environment for signs of malware, ransomware, and other infectious attacks.
Enterprises normally deploy both firewalls and antivirus programs. As complementary solutions, they each provide essential protective layers for safeguarding business assets.
Firewall Functions: NAT And VPN
Network Address Translation (NAT) and Virtual Private Network (VPN) are two distinct technologies, each with its own set of functions related to network security and connectivity. While NAT is primarily associated with address translation for routing purposes, VPNs are used to create secure, encrypted connections over the internet.
NAT
NAT changes the destination or source addresses of data packets as they pass through a firewall. This allows multiple devices to connect to the internet using the same IP address, which helps protect the private network from direct exposure to external threats.
In an office environment, each employee uses their own computer or mobile device to access the internet for browsing, emailing, and accessing cloud services. Despite each device having its own private IP address within the company's internal network, all outbound traffic appears to external networks as originating from the same public IP address assigned to the company. As a result, it’s harder for potential attackers to identify and target individual devices.
VPN
A VPN is a type of proxy server. Therefore, it serves as a barrier between a computer or network and the internet, receiving all web requests before forwarding them to the network.
VPNs are common and extend the private network across a public one, such as the internet. This allows users to securely transmit data as if their devices were directly connected to the private network. The connection establishes an encrypted tunnel between remote devices and the corporate network, enabling secure access.
This function is especially useful in a hybrid environment. Remote employees can leverage VPNs to access corporate networks and critical applications regardless of where or how they’re working.
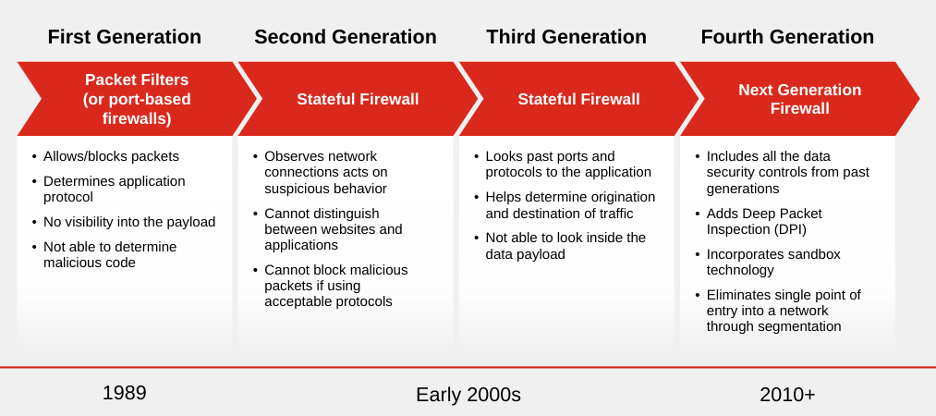
Firewalls have evolved through four distinct phases:
First-generation firewalls began in 1989 with the packet filtering approach. These firewalls examine individual data packets, making decisions to allow or block them based on predefined rules. However, these were unable to identify if those packets contained malicious code (i.e., malware).
Second-generation firewalls began in the early 2000s. Otherwise known as stateful firewalls, these track the state of active connections. By observing network traffic, they use context to identify and act on suspicious behavior. Unfortunately, this generation also has its limitations.
Third-generation firewalls emerged in the latter half of the early 2000s. Often called proxy firewalls or application-level gateways, these act as intermediaries between a client and server, forwarding requests and filtering responses.
Fourth-generation firewalls, also known as next-generation firewalls (NGFW), started in 2010. NGFWs combine traditional capabilities with new, advanced features such as intrusion prevention (IPS), application-layer filtering, and advanced threat detection.
Although each generation improved upon the last, many earlier iterations are still in use today. Let’s review the benefits of each firewall in more detail.

Next-generation firewalls (NGFWs) serve as gatekeepers to safeguard an organization’s compute resources with secure networking, advanced threat inspection and detection, and web filtering. Hybrid working models and the rapid adoption of cloud services are forcing network security to evolve to give enterprises complete visibility and control across the entire distributed infrastructure.
When evaluating NGFW solutions, potential trade-offs between security and performance may be top of mind. The ability to provide consistent and consolidated security protection across all distributed edges with minimal performance impact is critical. Following are six criteria to consider when evaluating NGFWs for a distributed security edge to edge.
6 Criteria for Evaluating NGFWs for High-Performance Security
-
Integrated AI-Powered Security Services
NGFWs that are tightly integrated with AI-powered security services provide real-time threat intelligence with multi-layered security that includes network intrusion prevention, malware scanning, and web filtering for comprehensive protection. AI-powered security services complement traditional firewall capabilities with proactive threat detection against evolving threats including machine learning. This reduces the workload for security teams, improves security efficiency and resource allocation, and streamlines security management for better decision making.
-
Threat Protection Performance
Threat protection performance is a measurement of how well an NGFW performs while running full threat protection, including firewalling, intrusion prevention, antivirus, and application control. It is critical for the NGFW to sustain high performance when full threat protection is turned on. Many NGFW providers are ambiguous about how they represent their threat protection performance claims. Documented performance claims should be examined carefully to ensure they reflect testing under load, with threat protection fully engaged.
-
Single-Pane-of-Glass Management
The management interface is where many security architects are stymied in their selection process. Careful attention may have been paid to the management system’s user interface and functionality, but if it is limited to the NGFW, security teams will have to toggle between multiple dashboards to assess vulnerabilities and respond to threats. End-to-end visibility and control are possible only if the NGFW is part of a broad, integrated security architecture, across which it can share threat information with other network devices and receive threat intelligence automatically.
-
Ensure a Broader Security Strategy
The hybrid workforce has forever changed the cybersecurity landscape. Many NGFW vendors have add-on SD-WAN, SASE, and ZTNA features to allow organizations with branch offices to build highly available and high-performance networks. Look for a vendor that offers fully integrated secure SD-WAN, SASE, and ZTNA capabilities in NGFWs that help consolidate their point products and enforce centralized control. This reduces overall investment costs, while eliminating security gaps.
-
Price/Performance and Other Operational Considerations
Some vendors scale performance by increasing the size, and consequently, the price of their NGFWs. This may not align with enterprise trends toward shrinking technology footprints. Aim for an NGFW that delivers the required performance in the most compact form factor. This not only reduces total cost of ownership (TCO) but also saves space and reduces energy consumption—both important objectives for environmentally conscious enterprises.
-
Independent Third-Party Validation
Although network security is a rapidly evolving industry, no enterprise can afford the risk of untested security innovations. Architects should not rely on vendor claims alone but seek third-party evaluation from recognized testing houses such as CyberRatings.org.
Choosing Your Firewall Deployment Use Cases
When choosing a firewall, consider the use case. Are you securing a branch office or ATM, a data center, or your headquarters on campus? Do you need to protect your network with work-from-anywhere access for remote users? Will your users need to access applications on multiple clouds? Do you need network segmentation to safeguard assets?
Deployment Scenarios:
- Branch – Protect and connect small offices or ATMs with AI/ML-powered security and convergence with secure SD-WAN.
- Campus – Gain visibility and protection of enterprise headquarters with the ability to manage applications, users, devices, and access from a single dashboard.
- Data Center – Deploy hyperscale security with consistent, coordinated protection, rich interfaces, and decryption that scales to any environment.
- Segmentation – Protect your assets with rich macro- and micro-segmentation to isolate potential threats and create secure zones.
- Multicloud – Integrate public and private cloud protection with easy-to-manage automation from a single console.
- Remote – Extend protection with converged networking and security services, including firewall-as-a-service and SASE cloud-native architecture.
Fortinet Products & Services
Fortinet provides consistent and consolidated secure networking across all distributed edges with minimal performance impact. This is critical to support hybrid work and cloud application services today. Fortinet's secure networking solutions include SD-WAN, ZTNA, NGFW, WLAN, and SASE to provide comprehensive network security and connectivity.
Key Features:
- Powerful Security and Networking Convergence: Integrated secure networking services like SD-WAN, ZTNA, and SSL decryption are included—no extra licensing required.
- Superior Price-Per-Performance: Custom-built ASIC architecture delivers high ROI with hyperscale support and ultra-low latency.
- AI/ML-Powered Threat Protection: FortiGuard Labs offers AI/ML-powered security services for advanced threat detection, anomaly discovery, and prevention of business disruptions.
- Central and Unified Management: FortiOS powers all dispersed network firewalls, with FortiManager providing a single pane of glass for granular visibility and control.
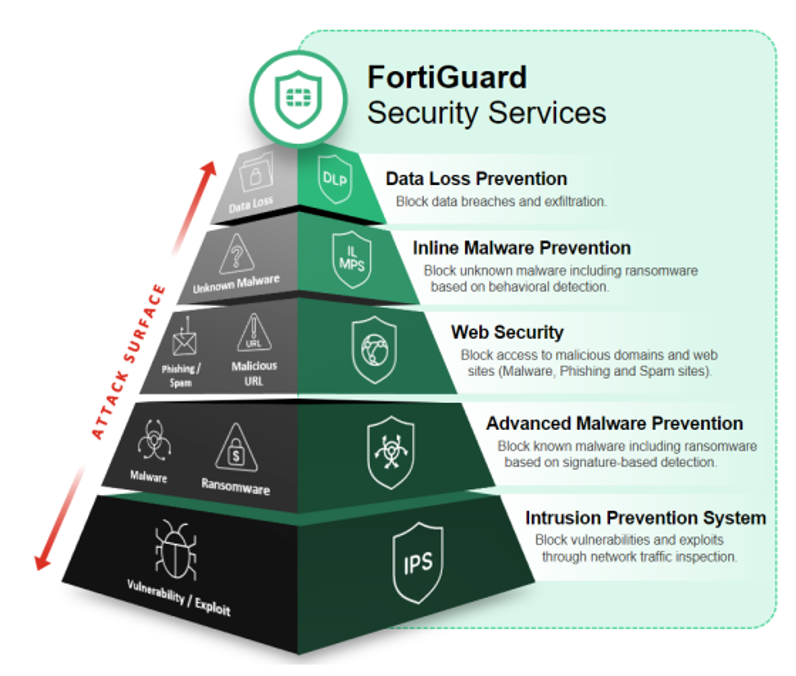
AI-Powered Security Services
FortiGuard AI-powered Security Services provide comprehensive security capabilities, delivering real-time threat intelligence for proactive protection. These services include:
- Advanced threat protection with intrusion prevention services
- Unified threat protection with web filtering and DNS security
- Enterprise protection for SaaS, data security, and inline protection from zero-day threats